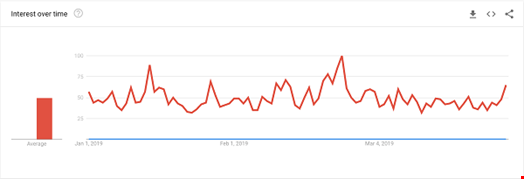
Shape Security is at Infosecurity Europe this year and we’re thinking about two topics trending in the United Kingdom: 1) the birth of the royal baby to the Duchess of Sussex, and 2) credential stuffing. Guess which one is represented by the red line in the Google Trends graph above? Yep, you guessed it, the red line is…Meghan Markle.
The flat blue line represents awareness of the epidemic of credential stuffing, a term coined by Sumit Agarwal, co-founder of Shape Security, during his time at the Pentagon. In a credential-stuffing campaign, an attacker collects thousands, millions, or, more recently, billions of username/password combinations and tests them against web login forms. Often the attackers are targeting a bank or hotel chain—but no site with a login form is safe.
The fact that nearly no one in the UK is Googling “credential stuffing” has us worried, because attackers know that credential stuffing is the easiest, most profitable threat vector out there today. Don’t believe us? On CSO Online’s “Hot or Not” list for 2019, credential stuffing is #1 of 11.
So how is it that the number-one threat vector for monetary cybercrime is going so unnoticed by the security community? Sure, we’d like to cast blame on the Royals for sucking all the oxygen out of the air, but they can’t help it. We suspect that the cause of the, um, “un-awaredness” is much more mundane: organizations simply aren’t set up to detect it.
Automated attackers have become incredibly sophisticated. Very often a victim organization is deluged with millions of login requests, but the requests are so small they don’t trip off any bandwidth alarms.
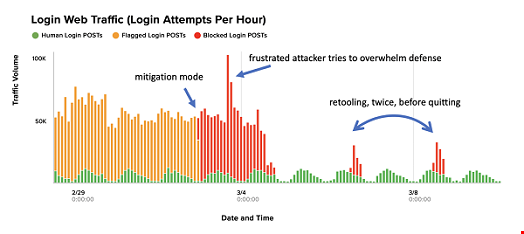
Here’s a graph of login traffic for a website under automated assault. The yellow bars represent all the login attempts that we flagged as probable automation; the victim organization had no idea and thought it was legitimate traffic. Once we showed them the cold, hard truth, they insisted we mitigate immediately.
What happened next was the same thing that always happens: the assailant redoubled his attack intensity, trying to get past mitigation, and then paused before retooling (twice) to attempt to get around the defences, and finally gave up. We see this pattern all the time.
If you’re attending our favorite conference, Infosecurity Europe, you may want to configure your site to collect some metrics before you leave. Turn on additional instrumentation for the following web forms on your critical applications:
- Login form
- Password reset
- Balance check (esp. if gift card)
What you’ll be looking for is the number of failed attempts as compared to the number of successful logins. High failure rates should be immediately investigated. Below are average login success ratios for one month of traffic across three major industries:
- Financial institutions: 79%
- Travel industry: 73%
- Retailers: 62%
Individual companies deviate from this average as much as 10%—the sites where customers log in more frequently tend to have a higher login-success ratio (because these passwords are remembered by browsers and password managers).
If you find abnormally low success rates (high failure rates), you should definitely come find Shape Security at Infosecurity Europe. We’ll be in the Discovery Zone, at stand X145.
The attacker community knows that credential stuffing is the number-one threat vector. We’re hoping that our participation at Infosecurity Europe this year will raise awareness among the defenders, so we can all put our mitigations in place and go back to cooing over whichever royal baby graces us with its presence next.
